Which of the Following Best Describes Spyware
It limits access to relevant levels of information. Which of the following best describes function creep.

What Is Spyware A Look At Spyware Examples Types
It monitors user actions that denote personal preferences then sends popups and ads to.
. Which of the following best describes spyware. Which of the following best describes spyware. Rootkit Spyware Trojan horse Botnet Privilege escalation.
This preview shows page 6 - 8 out of 31 pages. Question 14 - A user name and password are entered when logging onto a computer. Software that provides the originator with the venue to propagate.
C It is beneficial for society as a whole while raising dilemmas for consumers. Penetration testing involves attemp. Which of the following best describes spyware.
Software used for the collection of personal data. She performs analysis of the malware executable without running or installing it. A network device that filters access and traffic coming into a network.
Matty is examining malware as part of a security effort. B It has a ripple effect raising new ethical social and political issues. A software program deliberately created to harm your computer.
Spy planes sighted the buildup of. CIt monitors the actions you take on your machine and send the information back to its originating source. An attack that slows or crashes a device or network service.
While applying the access control matrix may be impractical an access control list can be employed as a solution. The use of stolen credentials to access private data. Instead she examines source and.
Which of the following best describes this infection. Software that reports data such as surfing habits and sites visited. What characteristic describes spyware.
For example by violating their privacy or endangering their devices security. It monitors user actions that denote personal preferences and then sends pop-ups andads to the user that match their tastes. You need to create a storage solution in Azure.
Which of the following statements best describes the null hypothesis The. Software used for the collection of personal data. 7Which of the following best describes spyware.
Software that reports data such as surfing. A hospital has received reports from multiple patients that their PHI was stolen after completing forms on the hospitals website. Which of the following best describes spyware.
It is a malicious program disguised as legitimate software. Which of the following best describes spyware. A It has a dampening effect on the discourse of business ethics.
When a company uses the technology intended for one purpose for a different purpose. A hospital has received reports from multiple patients that their PHI was stolen after completing forms on the hospitals website. A software program designed to detect and block viruses from infecting your computer.
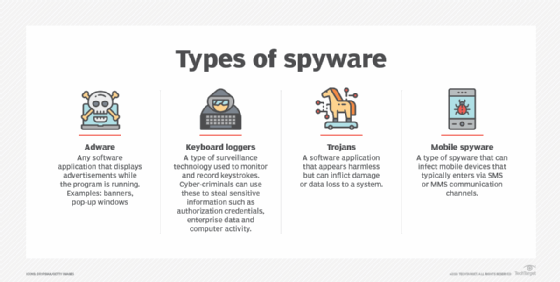
Spyware collects information from a target system Adware delivers advertisements with or without consent Bot waits for commands from the hacker Ransomware holds a computer system or data captive until payment is received. This behavior may be present in malware as well as in legitimate software. 2 Which of the following best describes the effect that new information technology has on society.
B It has a ripple effect raising new ethical social and political issues. Which statement best describes spyware. Which of the following terms best describes this software.
Restricting access to objects based on the sensitivity of the information contained in the objects is an example of. When a projects features keep being added to during development. When a user accesses data without authorization.
Soviet forces shot down US. You Might Also Like. AIt is a malicious program disguised as legitimate software.
Software that provides the originator with the venue to propagate. You plan to map a network drive from several computers that run Windows 10 to Azure Storage. Software hidden on a computer for the purpose of compromising the system.
100 6 ratings Part IThreat Management 1Attempts to uncover deep vulnerabilities and then manually exploit them 2Vulnerability scanning is performed using an automated tool to scan a network for known vulnerability signatures. Upon investigation the. When spyware collects and transmits data from a database.
Which of the following best describes function creep. Which of the following best describes spyware. Plus must operate independently.
Software hidden on a computer for the purpose of compromising the system. To pay in order to regain control and to clear the virus. A software program that secretly gathers information about users while they navigate the Internet.
Which of the following BEST describes malicious software that demands the end-user pay a fee or face the destruction of their files. It authenticates the user and gives access to all information. Software that is installed on a user device and collects information about the user.
We review their content and use your feedback to keep the quality high. BIt monitors user actions that denote personal preferences then sends pop-ups and ads to the user that match their tastes. Which of the following BEST describes the type of malware infecting this companys network.
Answer - cSoftware used for the collection of personal dataOracle ____ is an online analytical processing server that provides centralized management and advanced analytical capabilities eg budgeting forecasting. 1 440 364-0683 Spy group amateur video. Which one of the following is a feature of using a user name.
It monitors the actions you take on your machine and sends the information back to itsoriginating source. My best hypothesis is that someone hoped that public outcry would sway a wavering fifth vote. Spyware a portmanteau for spying software is software with malicious behavior that aims to gather information about a person or organization and send it to another entity in a way that harms the user.

What Are The Top 10 Spyware Threats

What Is Spyware A Look At Spyware Examples Types

11 Ways To Protect Windows Computers Webnots Windows Defender Windows Computer Computer Shop
No comments for "Which of the Following Best Describes Spyware"
Post a Comment